Introduction
Both SMB and NTFS permissions play a crucial role in setting up proper access to files and folders within a file server. There are some crucial distinctions to keep in mind to correctly set up permissions on a new file share or when delegating access to existing files and folders. In this document, we will review the basics of each, and best practice principles and applications in the real world.
SMB and NTFS
SMB (Server Message Block)
Server Message Block (SMB) is a network protocol that can be used to share files, printers and other resources across several operating systems. The most common use that you have probably run into is Windows Shared Folders.
To expose a folder to the network via SMB, simply go to the folder properties and select “Sharing” and set up the share name. Now, navigating to the resource URL+File Share name (for example \\SERVERNAME\SHARE) will take you to said resource.
When setting up the Sharing settings, you also have the option to edit SMB permissions (can be found under “Advanced Sharing”). In this menu, you can choose who can “see” the share. Any users/groups not listed here will not be able to see the share.
SMB Permission Types
There are three types of permission that you can find in the Permissions tab for the sharing options:
- Full Control: Users can read/write, as well as edit permissions and take ownership of files.
- Change: User can read/execute/write/delete folders/files within share.
- Read: User can view contents of share.
These permissions are not only applied to the top level of the share, but to all the folder/files within it. For example, if your SMB permissions for a share are set to CHANGE, your SMB permissions for all folders/files within the share will also be CHANGE.
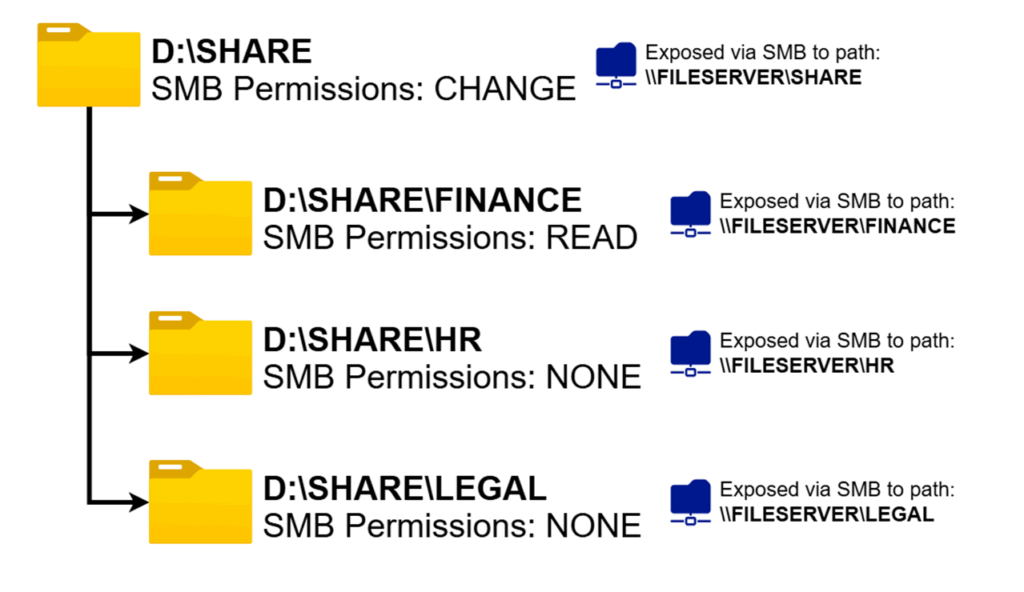
SMB Nested Share Issue
Things can however get a little messy if there are nested shares within each other (if a root folder is shared out and a folder underneath said root folder is also shared out). For example, look at the diagram following nested shares and the permissions set for a user.
Even though the user does not have direct access, for example, to HR folder, you inadvertently gave them CHANGE SMB permission to it since they can still access it through the root folder. This can become a big problem, but thankfully, in addition to NTFS permissions, we can resolve said issue.
SMB Permission are just one level of permissions, lets look at NTFS permissions, which give us a finer control of access.
NTFS (New Technology File System)
NTFS or New Technology File System, is a file system developed by Microsoft for storing, organizing and finding files within the Windows OS. The file system contains many features, but one of the most important is ACLs (Access Control Lists).
NTFS Permissions
ACLs are a list of ACEs (Access Control Entries) that define the permissions for a file or folder. We most commonly just refer to them as “Permissions”. NTFS permissions for a file or folder can be located under the Security tab in file/folder properties. There are a few different types of permissions when it comes to NTFS permissions:
- Full Control: Allows users to read, write, change, and delete files and subfolders. In addition, users can change permissions settings for all files and subdirectories.
- Modify: Allows users to read, write, change, and delete files and subfolders. In addition, users can change permissions settings for all files and subdirectories.
- Read and Execute: Allows users to view and run executable files, including scripts.
- List Folder Contents: Permits viewing and listing of files and subfolders as well as executing of files; inherited by folders only.
- Read: Allows users to view the folder and subfolder contents.
- Write: Allows users to add files and subfolders, allows you to write to a file.
NTFS Permission Options
In addition to permissions, there are a few other options you have when applying to a principal (a user, group or object). These can be found under Advanced in the Security tab.
- Type: The permission you could be setting up can either be an “Allow” (grant access) or “Deny” (Restrict Access). All DENY permissions will override any ALLOWs and not give permissions.
- Applies To: This can set the scope for the permission you are setting up for a folder. By default, it is set to “This folder, subfolders and files” (meaning anything downstream of the directory).
NTFS Inheritance
Another important feature to keep in mind is Inheritance. Opposed to share level permissions, NTFS permissions offer the possibility to let files and subfolders inherit NTFS permissions from their parent folders. The inheritance chain can be interrupted at any level, from the top down to a file, by disabling inheritance. If inheritance is disabled at a specific level, the object, either a file or folder will not inherit permissions from its parent folders.
SMB and NTFS Permissions and Effective Access
It may be confusing how SMB and NTFS permissions interact with each other and how they affect each other, but it’s actually a lot simpler than you think. Your “Effective Access” (i.e. the access you really have), in every case, is the most “restrictive” permission. Let’s run through a few examples:
Scenario 1
Scenario: You have Full Control SMB permissions and Read NTFS permissions
Result: Since your most restrictive permission is Read you will only be able to read said file or folder even though your SMB permission is set to Full Control.
Scenario 2
Scenario: You have None SMB permissions and Modify NTFS permissions
Result: Since you have no permissions to the share (SMB Permissions), you will not even be able to reach the file. (Though if you were to access the file by other means, such as locally on the server, or a different share, you’d be able to modify the folder/file).
Scenario 3
Scenario: You have Read SMB permissions and Full Control NTFS permissions
Result: Since you SMB permissions are set to Read, you will only be able to read the files/folders even though you might have Full Control through NTFS. (Though if you were to access the file by other means, such as locally on the server, or a different share, you’d be able to modify the folder/file).
Effective Access
Effective Access is often hard to figure out, especially if you have a complex organization or large file server, so Microsoft provides tools to allow you to view what kind of access a user or group has to specific files/folders.
In the Advanced Security section of a file or folder you’d like to check permissions for, navigate to the Effective Access tab. Select the user/group/object you would like to test and click “View Effective Access”. The result should be a list of permissions with either “Allowed” or “Denied”. Permissions can be denied for two reasons: File Permissions (NTFS) or Share Permissions (SMB).
Best Practices
There are a few overarching themes across best practices when it comes to setting up/assigning SMB and NTFS permissions.
SMB vs NTFS Permissions
When setting up permissions, it can become difficult to keep track of Effective Access if you have different SMB and NTFS permissions. There are generally two schools of thought when it comes to working with both of them:
Easy Way
Grant Full-Control Share access to the groups/users you wish to assign permissions to and then use NTFS to lock down access from there. Using this would make it easier to set up permissions as you are now only worried about one set of them (NTFS). This is still secure as the lower NTFS permissions will lock down the user’s ability in terms of what they can do.
The only time this can become unsecure is when the protocol itself (SMB) or associated authentication protocol (NTLM) is vulnerable (It has happened and is still vulnerable to several attack vectors such as stolen hashes, etc). If that’s the case, a bad actor can use said vulnerabilities to give themselves access or permissions to shares (which can then allow them to further jump around in an environment, potentially undetected) using the Full Control permission.
Secure Way
The most secure way is to have your SMB and NTFS permissions match for a particular group of users or groups. To be clear, if SMB or the associated authentication protocol is vulnerable (has a bug, glitch, etc.), a bad actor could still get in, but they’d have less permissions (as you wouldn’t be granting Full Control access across the board for every share). This can become difficult as you have to keep track of more shares with two sets of permissions.
Importance to Security
It’s important to have these permissions set up properly because all it can take is one opening for a threat actor, and it can cause a compromised network. Making sure these permissions are set up correctly and securely is crucial to an organization’s cybersecurity posture.
Organization
Adding/modifying permissions for a principal (whether that be a local object or a domain object such as user, group or computer) should be easy. You should not have to change folder/file permissions as modifying a lot of files could take a long time. Instead, Groups should be used to minimize how long it takes to grant/deny permissions.
For example, if there is a Finance folder within a file share and a new finance employee gets onboarded, you should only need to add said employee to the Finance group (that has permissions to the folder), instead of modifying the NTFS permissions to include the new employee.
- NOTE: When working in AD environments, that group memberships only apply to a user after they have logged out and back in, otherwise their current session will not reflect their group membership properties.
Principle of Least Privilege
In cybersecurity, the principle of least privilege means that one only has access to what they need. When setting up permissions, it’s important to limit the scope of access across the organization. You should never assign permissions to company/private files using Principals such as: Everyone, Domain Users, Authenticated Users, Guests. These all pose a significant risk to security and must be avoided if possible.
Conclusion and Resources
Overall, understanding and setting up SMB/NTFS permissions properly is crucial for efficiency and security. Here are a few of the resources I used to create this document and use as references: